Azure Service Endpoints
Table of contents
No headings in the article.
Azure service endpoints are like secret tunnels that connect your virtual network to Azure services, and they help keep your stuff safe by only letting the right things through.
Imagine you have a magical treehouse 🌳🏠:
Treehouse: Your treehouse is like your computer, but it's way up in a big, magical tree (that's the cloud).
Special Rooms: Inside your treehouse, you have different rooms for different things. One room is for storing your toys, another for keeping your secret diary, and one for your snacks.
Friends and Safety: You have some friends who live in the same treehouse. You trust them and want them to come to your rooms, but you don't want strangers to come in.
Now, here's where Azure service endpoints come in:
Service Endpoints are Magical Doors 🚪✨:
Service Endpoints: Think of service endpoints as special, magical doors that connect your treehouse to other magical places (like the candy store, toy store, and library).
Toy Store: Let's say you have a toy store in the cloud (that's an Azure service). You want your friends in the treehouse to be able to get toys from there, but you don't want anyone else in the cloud to sneak into your treehouse.
Setting Up Service Endpoints: So, you create a magical door (that's the service endpoint) between your toy store and your treehouse. Only your trusted friends can use this door because you've given them the magical key.
Safety First: With this magical door, your toys are safe because only your friends in your treehouse can access them. Strangers can't just walk in because they don't have the magical key.
Other Rooms: You can do the same for your snack room, diary room, and any other room you want to connect to the cloud. Each room has its magical door that only your trusted friends can use.
So, Azure service endpoints are like magical doors that connect your treehouse (your computer in the cloud) to different places (Azure services) in a safe and secure way. They make sure only your trusted friends (or devices in your virtual network) can access those places, keeping your things safe and sound!
----------------------------------------------------------------------------------------
Service endpoints enable us to link specific platform services with our virtual networks (our treehouse). As a result, our Azure virtual machines can communicate with Azure SQL and Azure Storage accounts as though they were components of the same virtual network, instead of accessing them through the public endpoint.
Configuration
Configure service endpoints on a subnet in a virtual network. Endpoints work with any type of compute instance running within that subnet.
You can configure multiple service endpoints for all supported Azure services (Azure Storage or Azure SQL Database, for example) on a subnet.
For supported services, you can secure new or existing resources to virtual networks using service endpoints.

Effective routes show us what networking routes this particular virtual machine will know about, so I took a screenshot before enabling the service endpoint as well as after.
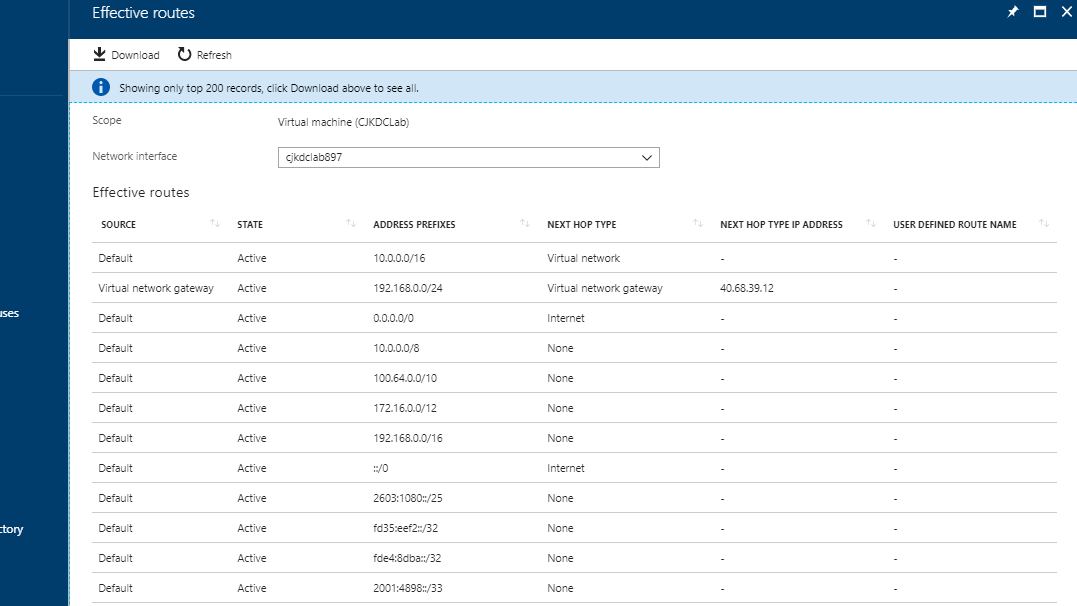
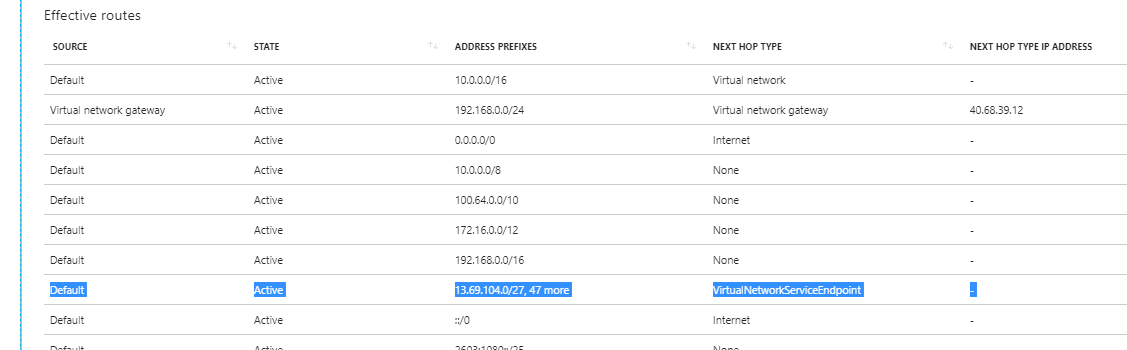
When comparing, I've noticed a new route that has been received from the subnet. This fresh route encompasses the complete public IP range allocated for the Azure SQL Server service. It guides traffic, specifying that to reach any destination within these ranges, it should travel through a "virtual network service endpoint." This means the traffic will enter the Azure network and be directed to our Azure Storage instance, rather than taking the previous route out through the public endpoint.
Now it’s important to state that using service endpoints does not remove the public endpoint from Azure SQL or Azure Storage accounts – it’s just a redirection of traffic. So, while we have traffic over the new virtual network service endpoint for a particular subnet, anything outside of that subnet will still access the Azure SQL Server, SQLDBs or Storage account over the public endpoint(s); so we need to have our Azure Storage and Azure SQL firewalls white/black listed appropriately.